| Home |
| Misc |
| Linux |
| TCP/IP |
| Windows |
| Random Daodejing |
| Photos |
TCP/IP Notes
Intro / Network Addressing / Network Addressing IPv6 / Packet Headers / Networking and Data Link Layers / Transport Layer Protocols / Application Layer Protocols / IP Routing / ICMP / DHCP / Name Resolution and DNS / Security
SECURITY
The basic protocols supporting the TCP/IP environment were lacking in security features when first developed, prior to the WWW when networking was new and not as widespread.
Much of securing TCP/IP networks is in addressing the holes and points of attack left open by these protocols. This involves keeping up to date with security vulnerabilities and performing regular assessments.
Network Security Basics
--------------------------------
The security transaction can be viewed as an attacker and a victim. Hackers may pose no real threat (interested in bragging rights, intellectual challenge or exploration rather than destruction), or they may intend to cause damage, theft and harm. Crackers (malicious hackers and script kiddies) may lack deep knowledge of networks and systems but are capable of using automated tools and scripts to exploit points of weakness.
Security also involves data integrity and mitigating against damage to data and system configuration whether intentional or accidental. This includes disaster recovery planning and backup procedures.
Network security focuses upon three major areas:
Physical security - Physical security involves taking steps to prevent unauthorized physical access to servers, routers, firewalls and other equipment. Authorization of access may include card keys, biometric access & ID badges.
Personnel security - This involves informing personnel of security matters and properly training them, as well as establishing organizational security policies which document requirements for security practices, rules and procedures.
One example would be to train personnel in social engineering techniques.
System and Network security - Analyzing the current environment and identifying and eliminating or mitigating exploits and points of attack.
Principles of IP security
-------------------------------
Avoid unnecessary exposure - Don't install unused or unnecessary IP-based protocols or services, especially on firewalls or other outward facing devices.
Block all unused ports - Use a port scanner to do a security audit and analyze which ports are open (from where and to where).
Prevent internal address spoofing - A packet which claims to originate inside of a network shouldn't be found at a router or firewall interface from external traffic entering the network.
Filter unwanted addresses - Reject packets from certain domains provided by subscriber services.
Exclude access by default, include access by exception - AKA 'pessimistic security model' or deny-by-default policy.
Restrict outside access to "compromisable" hosts - Any time resources, services or information is exposed, attacks should be expected as well as the ability to recover without loss of service or data. In other words, restrict public-facing interfaces to hosts which will not jeopardize the entire organization if compromised.
Protect clients and servers from obvious attacks - Includes antivirus, antispyware, pop-up blockers, application and operating system security patches. Outside USB sticks, Malware embedded in Adobe PDF documents sent via email and email phishing attempts are but further examples.
Attack your own systems - In addition to regular maintenance and keeping up to date with security vulnerabilities and exploits, consider hiring an outside firm to perform penetration testing and other procedures to audit the effectiveness of security policies and procedures.
It is often said that security is the journey rather than the destination, as technology and vulnerabilities and bugs and exploits are constantly changing and emerging and mutating.
Key Weaknesses in TCP/IP
----------------------------------
IP, TCP and UDP among other fundamental protocols offer no built-in security controls. One of the first major weaknesses this offers to attackers is the knowledge that implementation problems may exist within a given system.
The goal of TCP and UDP ports on a host are to allow points of entry for legitimate access to IP-based services. These same ports can also be compromised. This leaves many ways in which attackers can exploit TCP/IP:
The impersonation of valid users (especially root) via brute force or by other means.
Session hijacking - Inserting IP packets into an existing communication.
Packet sniffing - Using a protocol/packet analyzer to discover unencrypted account and password information in transit.
IP spoofing - Where an attacker sends packets to a target host but substitutes the IP address of another host, used to bypass access control lists on a router or within the host itself (e.g., spoofing a host with windowsupdate.microsoft.com).
DoS attack - Crippling a server by sending too much traffic for it to handle.
Flexibility vs. Security
----------------------------
Designers of TCP/IP protocols have made them as flexible as possible to be able to work together, however much of the features provided by this flexibility are also points of weakness from a security point of view. For example a proxy ARP function can be used to allow hosts to communicate across a routed network without having default gateways manually configured, but this also allows an attacker to redirect traffic from a host to another machine via illegitimate proxy ARPs.
Common Types of IP-Related Attacks
-------------------------------------------------
Man-in-the-middle (MITM) - Attacker intercepts traffic from both parties to eavesdrop or forge a reply from either end.
IP service attacks - Affects numerous IP services (e.g., HTTP, FTP), often occurring through well-known ports.
IP service implementation vulnerabilities - Bugs or out-of-date patches within specific implementations of IP services on particular platforms.
Insecure IP protocols and services - These can include unencrypted communications (FTP & Telnet). Restricting public access or switching protocols to more secure versions (SSH, SFTP) or tunneling traffic through a secure VPN are recommended strategies.
Which IP Services are Most Vulnerable?
----------------------------------------------------
Remote login services - Includes telnet, Berkeley r-utils, Windows RDP, LogMeIn, GoToMyPc, etc.
Anonymous access services - FTP and web services. A separation between public-facing and internal data is recommended.
Phases of IP attacks
---------------------------
IP attacks often follow a pattern which begins with network discovery, in which the attacker learns about active systems and services offered. Once sufficient research is done an attack can be formulated and launched, whether a break-in through planting a malicious piece of software (or exploiting a known vulnerability) or by disrupting host operations via DoS.
Reconnaissance and Discovery - Generally begins with a simple PING or scan via Nmap to check for open ports. A ICMP Echo Request is sent to the targeted network to identify active hosts/services. To escape immediate detection an attacker might vary destination port number or interpacket time. The location of the attacking host may also be disguised via multiple proxies or compromised zombie hosts.
Attack - Once vulnerabilities are determined, attempts at exploiting them can be launched.
Cover-up - The attacker attempts to leave no trace behind by editing log files etc.
Common Attacks and Entry Points in More Detail
-----------------------------------------------------------------
Viruses, Worms, Trojan Horse programs - Malicious code known as malware which serves to disrupt or corrupt data or operations.
Adware and Spyware - Adware can allow a compromised machine to display unsolicited advertising, while spyware (which might also be adware) can use stealth to take up unauthorized occupancy within a machine, capable of gathering user information and sending this information to a remote location.
Denial of Service (DoS) - Designed to overload and overwhelm the operations of network devices and communications, denying service to users or hosts on a network. DoS-related attacks include SYN floods, broadcast amplification attacks, and buffer overflow. These attacks are less complicated than others, and the underlying protocols do not enforce rules against 'operational exploitation.'
Distributed Denial of Service (DDoS) - DoS attacks launched from numerous devices, consists of four main elements:
- Attacker
- Handler (Master/Manager)
- Agent (Slave/Zombie)
- Victim
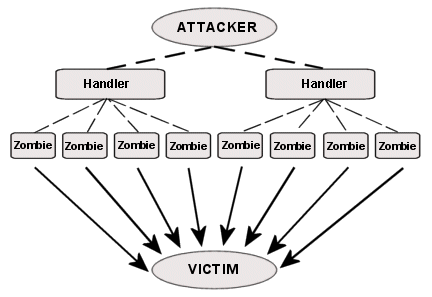
An attack can be set up in advance, to where the original attacker is not even present once the attack is launched. Once a host is targeted, it becomes the handler for the attack. The handler then locates other insecure hosts to act as agents. There are other variations on this method of attack (see Further Reading).
Buffer Overflows/Overruns - Exploits a weakness in programs which expect to receive a fixed amount of input. When more data than is expected is sent, the input of the program's buffer overflows. It is recommend to disassociate users from system, administrator, or domain administrator accounts, and to run certain services (e.g., IIS) on other user accounts which lack administrative rights.
Spoofing - Borrowing identity information (IP address, domain name, NetBIOS name, TCP/UDP port numbers, etc.).
TCP Session Hijacking - Masquerade as an authorized user to gain system access or pry sensitive information in an active communication session. The attacker must successfully communicate with client and server simultaneously while predicting the next TCP sequence number to spoof the source address on packets to client and server so that it appears to the client that the attacker is actually the server. The attacker can also send packets to a server to execute commands or change passwords.
Network Sniffing - Eavesdropping on unencrypted network communications using a protocol/packet analyzer (Wireshark, tcpdump, etc.). Conversely there are also anti-sniff software packages available to alert to the presence of packet sniffers on a network.
Maintaining IP Security
------------------------------
Security often involves trade-offs, but as routine practice the following procedures may be considered:
Applying Security Patches and Fixes - Many attacks take advantage of vulnerabilities inherent in operating systems and application software (as well as 'zero-day exploits'). These often come in the form of newly discovered security holes which may be exploited before a patch is implemented. The first step is to be aware and up to date on vulnerability warnings. For Windows operating systems, the best place to go for this information is the Microsoft Security Bulletin (https://technet.microsoft.com/en-us/security/bulletin). Microsoft Technical Security Notifications via e-mail can also be received at: https://technet.microsoft.com/en-us/security/dd252948. Also, it is important to be aware of security updates for various types of programs which may be used on inter-network machines, such as Adobe software, Java, and Flash.
Security Update Process
---------------------------------
1) Evaluate the vulnerability - Operating system, antivirus definition updates, and software security updates.
2) Retrieve the patch or update.
3) Test the patch or update - Prior to full-scale deployment, it is important to test the updates or patches to check for failure, performance degradation, incompatibility issues etc.
4. Deploy the patch or update.
Knowing Which Ports to Block
---------------------------------------
Below are recommended ports to block, adhering to the pessimistic model (deny-by-default):
TCP 21 - FTP
TCP 22 - SSH remote login
TCP 23 - Telnet
TCP 25 - SMTP
TCP 53 - DNS
UDP 53 - DNS
TCP 110 - POP3
TCP 111 - RPC
TCP 143 - IMAP
UDP 161 - SNMP
Using IP Security (IPSec)
---------------------------------
IP Security (IPSec) is an optional add-in security layer to IPv4 networks defined by the IP Security Protocol Working Group (IPSEC). It includes numerous components to provide cryptographic security services, strong authentication, and integrity and access controls. Although optional in IPv4, it is a required part of IPv6. Defined by RFC 2401 (https://tools.ietf.org/html/rfc2401), the goals of IPSec are to provide:
Access control - Restricting permissions to resources including bandwidth and information. To support this IPSec uses authentication and access controls.
Connectionless integrity - Integrity specifies that a communication remains unchanged, and connectionless specifies that integrity does not extend to the connection itself (e.g., detecting packets arriving out of sequence). To support this IPSec uses authentication.
Data origin authentication - Verify that data received comes from the named source. To support this IPSec uses authentication.
Protection against replays - Places unique and frequently changed token in each communication, invalidating previously used tokens in new communications. To support this IPSec uses partial sequence integrity.
Confidentiality - Prevents unauthorized communication viewing. IPSec supports this by using encryption tools.
Limited traffic flow confidentiality - Hiding the path between communication ends. IPSec supports this through tunneling.
Among other security protocols used by IPSec, two of the most noteworthy are the Authentication Header (AH) and the Encapsulating Security Payload (ESP) Header. AH is able to determine the true origin of a packet to prevent address spoofing and session hijacking. IPSec also focuses on the use of keys to aid in security, including Internet Key Exchange (IKE) protocol, Internet Security Association and Key Management Protocol (ISAKMP), IP security Domain of Interpretation (DOI) for ISAKMP and other tools, as well as encryption and compression algorithms.
Protecting the Perimeter of the Network
------------------------------------------------------
Bastion host - Hardened computer specifically designed to resist unwanted attempts at entry, placed between the internal and external networks. Can include firewall service, proxy, and Intrusion Detection (IDS) capabilities. The computer should run only software required to support the role of protecting network boundaries.
Boundary (or border) router - AKA screening router. Placed between networks (usually internal and public-facing), between firewall and boundary. Can be used to filter inbound and/or outbound traffic on the basis of IP addresses, domain names, socket addresses, port numbers, and requested protocols and services.
Demilitarized zone (DMZ) - Usually placed between firewall and screening router (or between internal network and the outside world using sandwiched firewalls) accessible to both inside and outside. Acts as a sandbox or buffer area.
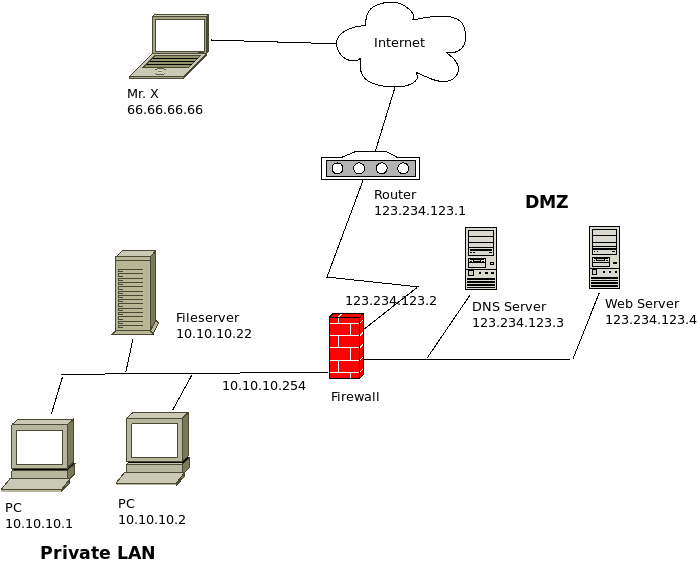
Firewall - Hardened software or hardware which places a barrier between internal and external traffic, inspecting and controlling traffic flow. Operates at Internet, Transport, and Application layers, enabling the inspection of IP packet payloads, domain names, IP and port addresses, and the detection of higher-level attacks. Can include proxy server software and IDS.
Network address translation - Specified in RFC 1918 (https://tools.ietf.org/html/rfc1918). Allows internal network addresses to translate into public network addresses when packets leave the internal network, protecting network addressing scheme. NAT is often used with private IP addresses.
Proxy server - Intermediary between user and end-server.
Screening host - Outside users to a network connect to a firewall which connects to the network through a proxy. It appears as though the firewall host is screening.
Major Firewall Elements
--------------------------------
Firewalls are like routers in that they must have at least two network interfaces. Firewalls usually incorporate four major elements:
Screening router functions - Permits firewall to block or filter traffic according to defined criteria.
Proxy service functions - Permits firewall to place itself between networks, protects address privacy, NAT services.
"Stateful inspection" of packet sequences and services - Makes decisions to allow or deny packets based on other packets. More sophisticated than a screening firewall which doesn't compare packets. Does not allow TCP packet with SYN-ACK flag unless previous packet using the same source and destination had the SYN flag set. Also does not allow ICMP Echo Reply to pass unless a previous ICMP Echo Request was sent.
Virtual private network services - Tunneling communications, often with encryption.
Proxy Servers
-------------------
Proxy servers can be thought of as dispatchers between internal network clients and external network servers. The goal of a proxy server is to mask the client IP address and forward communications to the external server; When the external server returns communications the process works in reverse. Proxy servers can also be used for reverse proxying, in which external clients request resources from internal servers. This can serve to screen addresses on the public Internet and prevent external users from direct access to internal resources.
An important proxy behavior is caching, in which the proxy server can store resources locally, which can improve performance for multiple users requesting the same resources. However there may also be cache-related exploits to be aware of.
Implementing Firewalls
-------------------------------
Security policies operate on a continuum between totally paranoid and totally optimistic. For example on one extreme some ultra-secure networks do not connect to the public Internet at all, and even disable access to other internal networks which have this capability. On the other end, it is entirely irresponsible to have no security policy. When planning and implementing firewall and proxy services the following steps might be useful:
1) Plan - Research and assess the needs of the organization, then do the same for the hardware and software available. Information sources such as security advisory groups and other neutral sources of information should be pursued. Some vendors may offer training or consulting services, but sticking entirely with vendor-specific information might not be as desirable, as vendors might tend to hide the bad news and overly-promote the good news.
2) Establish requirements - Based on the characteristics of the network environment, including deciding what traffic to allow and deny.
3) Install - Install hardware and software, but place the firewall outside of the main production environment boundary (in a controlled environment, out of public reach).
4) Configure - Analyze the default configuration and alter these to meet requirements. Make sure the software is up to date.
5) Test - Compare configuration settings to requirements.
6) Attack - Run a port scanner/packet analyzer. Inspect wireless networks also. The goal is to see how the system responds to an attack.
7) Tune - Refine configuration, and repeat steps 5-7.
8) Implement - Place the firewall on the network boundary.
9) Monitor and maintenance - Monitor event logs, traffic statistics, and error messages. Keep up to date with mailing lists and security newsgroups, and with vendor-specific updates, patches and fixes.
Role of IDS and IPS in IP Security
--------------------------------------------
An Intrusion Detection System (IDS) inspects patterns of network traffic for signs of attack. IDSs can automate recognition of and respond to potential attacks and other suspicious network traffic behavior in real time, performing statistical analysis to form a picture of what the network traffic 'should look like' as a baseline. Most IDSs will disconnect a user connection which displays suspicious traffic patterns and run a reverse DNS lookup for identification, and are capable of sending e-mail alerts and gathering records of suspicious network traffic. IDSs can also detect slow break in attempts and deal with DoS attacks. Many firewalls are able to interact with IDSs (or include built-in IDS functionality).
A related class of software is known as Intrusion Prevention Systems (IPS). While IDSs are passive and monitor/log, prevention systems are more proactive and can be used to recognize and foil attempts at break-in and pre-attack behaviors such as footprinting. IPSs can make access control decisions at the Application Layer, and can be used in tandem with IDSs.
Honeypots and Honeynets
-----------------------------------
The goal of honeypots and honeynets is to divert attackers, and to entice and trap. Although a honeypot may appear to be part of a network, it is often isolated but full of information and resources intentionally designed to look attractive to attackers. They may be useful for surveillance and also to provide an early-warning of potential attacks.
Honeynets broadens the honeypot concept but applies it to an entire fake network.
Further Reading
---------------------
The Many Faces of DDoS: Variations on a Theme or Two
https://devcentral.f5.com/articles/the-many-faces-of-ddos-variations-on-a-theme-or-two
Physical information security
https://en.wikipedia.org/wiki/Physical_information_security
Social Engineering Fundamentals, Part I: Hacker Tactics
https://www.symantec.com/connect/articles/social-engineering-fundamentals-part-i-hacker-tactics
How are spoofed packets detected?
https://security.stackexchange.com/questions/31999/how-are-spoofed-packets-detected
SecLists.Org Security Mailing List Archive
https://seclists.org/
SANS Reading Room
https://www.sans.org/reading-room/
Intrusion Detection Systems (IDS)
https://www.tldp.org/HOWTO/Security-Quickstart-HOWTO/intrusion.html